User Guide: Identity > How to Configure App Session Settings
How to Configure Identity Session Timeout and HTTP Message Body Integrity
Volt MX Foundry supports configuring session timeout (idle timeout and fixed timeout) for an app identity session. In Apps, Volt MX Foundry supports configuration of Identity Session Idle Timeout that applies across all of your apps, as well as support for Enable HTTP Message Body Integrity Checking for an Application. The following procedures describe how to configure session timeout and client app security.
Important: HTTP Integrity does not support Scheduler job.
How to Configure App Session Settings
You can configure either an idle timeout or fixed timeout for apps in the Applications > Identity page.
- Idle Timeout: Specifies the number of minutes that a session can remain idle before Volt MX Foundry automatically terminates the app.
- Identity Session Idle Timeout: When an app session on a device remains idle for a certain period of time, the app session expires automatically. The user will need to log into the app again.
- Maximum Session Duration: An apps log-in session is active until the maximum session duration time is met.
- Fixed Timeout: Specifies the session’s idle timeout (HH:SS) of an app. When the timeout is reached, the session expires automatically, and the user will need to log into the app again.
To configure an Identity Session Idle Timeout, do the following:
- Click on an app in the Apps, and then in the Identity tab, click the SERVICE CONFIGURATION button.
-
In Identity Session Timeout, do either of the following:
- Click the Idle Timeout.
- Enter the hours/seconds (HH:SS) in the Identity Session Idle Timeout.
- Enter the hours/seconds (HH:SS) in the Maximum Session Duration.
Or
- Click the Fixed Timeout, and enter the hours/seconds (HH:SS) in the Fixed Identity Session Duration.
- Click the Idle Timeout.
-
Click Save.
- Publish or republish the app to reflect the changes.
How to Enable HTTP Message Body Integrity
The Client App Security feature helps to secure data exchanged between a client app and a server app. Enterprise class applications may need to ensure that network traffic being exchanged between the server and client app is not tampered with. This feature detects and reports network traffic tampering on the data exchanged between the server and client app.
To enable HTTP Message body integrity for an Application, follow these steps:
-
Click on an app in the Apps, and then in the Identity tab, click the SERVICE CONFIGURATION button to display the Client App Security section.
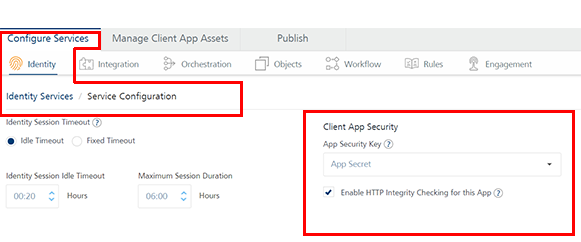
The App Security Key is used for HTTP Message body integrity checking and other client security features managed by the client app SDK.
-
In the App Security Key, you can select the default app security key or generate a custom security key. To select an app secret key, follow these steps:
-
From the App Security Key, select App Secret. The App Secret is selected by default.
-
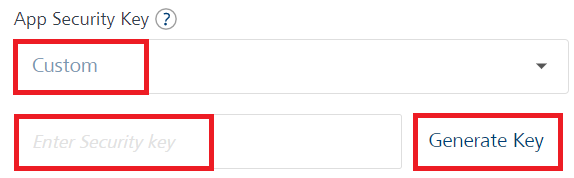
If you want to generate a custom key, select Custom from the App Security Key list.
-
Enter the custom security key and click OK. Otherwise you can generate a custom security key by clicking the Generate Key. A security key is generated.
Note: For more information, refer Usage of Custom App Security Key.
-
-
Select the Enable HTTP Integrity Checking for this App check box.
The HTTP Message body integrity Checking signs the outbound HTTP requests from a client application and verifies in inbound HTTP response signature to further enhance the security between the client app and backend services.
-
Click SAVE.
Note: More details to configure CORS and Identity Session Timeout in APIs