Additional Considerations
Configure Foundry Reporting and Analytics
JasperReports Server Professional Edition is a prerequisite to configuring Reporting and Analytics on Foundry. After you successfully set up the JasperReports Server, refer to the Volt MX Analytics and Reporting Installation Guide.
Logging Considerations
All the Foundry component pods generate logs, which are routed to the standard output (STDOUT). You can use the Fluent Bit plugin to capture these logs and route them to Amazon CloudWatch for log analysis.
To configure logging for pods that are deployed in Managed EC2, refer to the following blog post: Analyze Kubernetes container logs using Amazon S3 and Amazon Athena. To configure logging for pods deployed in the Fargate profile, refer to the following blog post: Fluent Bit for Amazon EKS on AWS Fargate is here.
In case you want to set up a mixed data plane, you need to use a combination of both approaches. For more information about the configurations that can be used, refer to the samples/Logging folder in the FoundryKube.zip file that you downloaded.
Monitoring Considerations
You can use CloudWatch Container Insights to manage metrics and logs from your container applications and microservices. Container Insights is available for Amazon Elastic Container Service (Amazon ECS), Amazon Elastic Kubernetes Service (Amazon EKS), and Kubernetes platforms on Amazon EC2.
CloudWatch collects metrics for resources such as CPU, memory, disk, and network. Container Insights also provides diagnostics such as container restart failures, which can help you isolate issues and resolve them quickly. You can also set alarms on the metrics that are collected by Container Insights. For more information, refer to following documents.
Caching Considerations
Amazon provides the ElastiCache service if your application needs a caching service. For production grade deployments, Volt MX recommends that you use caching to reduce load on your Foundry run-time services such as Integration and Identity. For information about setting up ElastiCache, refer to the ElastiCache for Memcached User Guide.
After you complete the setup, edit the Identity and Integration configmaps as described in the following sections to complete the configuration.
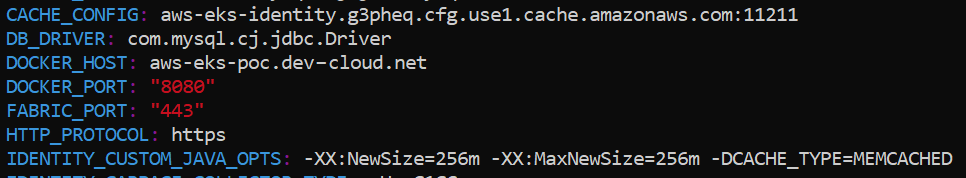
Identity
- Add the following key-value pair:
CACHE_CONFIG: <Identity Memcached cluster hostname:port> - Append the following -D parameter to the
IDENTITY_CUSTOM_JAVA_OPTSvalue:
–DCACHE_TYPE=MEMCACHED
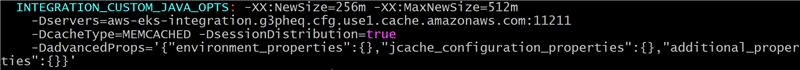
Integration
Append the following –D parameters to the INTEGRATION_CUSTOM_JAVA_OPTS value:
-Dservers=<Integration Memached cluster hostname:port>-DcacheType=MEMCACHED-DsessionDistribution=true-DadvancedProps='{"environment_properties":{},"jcache_configuration_properties":{},"additional_properties":{}}'
Encrypt the Database Password
Important: Encryption is only supported for Tomcat application servers.
Volt MX Foundry provides a 256-bit AES/GCM/NoPadding encryption utility, which can be used to encrypt your database password. To encrypt your database password, follow these steps:
- After you download and extract the installation zip file, navigate to the
libfolder. -
From the
libfolder, open a terminal (console), and then execute the following command:java -jar EncryptionUtility.jar -
In the Enter Password to be Encrypted field, type the password that is used to access your database.
- In the Enter Key to be Encrypted field, type the key that must be used to encrypt the password.
The console then displays the Encrypted Password and Encrypted Key. These values must be added to the DB_PASS and DB_PASS_SECRET_KEY parameters in the config.properties file. For more information, refer to Database Details.