Security
Good security is not a one-trick pony, but a combination of factors. Here is what we implemented:
- We use Open Standards wherever appropriate. Standards enjoy more scrutiny from more eyeballs.
- The vert.x Framework supports all flavors of SSL certificates.
- All endpoints, short of login and OData, require a signed JWT claim.
- We support public/private keys for identity provider setup.
- Databases are not automatically exposed on REST, when you run KEEP. Only the ones that are configured by the administrators.
- No anonymous access is granted for REST data.
- Access to sensitive information can be limited to servers that present additional credentials.
- Read/Write access is controlled on a per form, field and user basis. See The Barbican for details.
Here’s a flowchart to show how KEEP handles security.
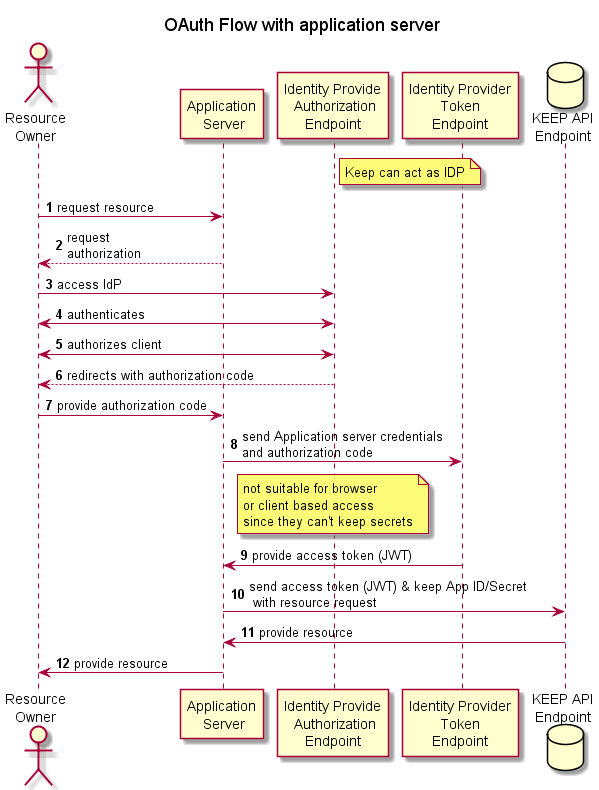
See more details in security configuration.
Table of contents
- Auth*
- Configuration parameters
- Configuring certificates
- Configuring identity provider
- Configuring Keycloak
- Securing KEEP endpoints
- config.json
- Encryption Keys
- KEEP SAML configuration
- security.json
- HTTPS - multi domain
- HTTPS - single domain
- Custom IdP
- KEEP IdP & Foundry