Set up external IdP for Office Round Trip Experience
Client Ids
When configuring an external IdP using OIDC or OIDC-idpcat, you need to provide a clientId. It's recommended to use Domino, but the admins of your IdP might have other ideas. In any case, that's the clientId for the REST server. It's NOT the one for the Admin UI or the Office Forms Based Authentication (OFBA) for attachment editing. To be fully operational, you need to configure at least three clients on your IdP:
Dominofor the server (client secret might be handeled byidpcat.nsf).keepadminuifor the Domino REST API admin client. If you also want to use your IdP for Domino REST API Admin UI login.keepofbafor the Office document round trip experience. If you also want to use your IdP for Domino REST API OFBA round trip editing authentication.- One each for your custom client applications (with clientSecret for servers or PKCE for clients).
Use the internal IdP as learning resource
The application configuration provided by the internal IdP makes it easy to configure and retrieve client-specific JWT that have all the required fields. Test your application with that and use the defined properties, scopes foremost, to requests the external IdP client configurations.
About this task
Aside from the default Domino REST API login page, you can also use your configured external IdP for Office Round Trip Experience log in.
Configuration
Set up external IdP
Configure your external IdP in the configuration file. For more information, see configuring external IdP for configuring an external IdP of your choice.
Note
When configuring your external IdP, make sure to set {{ origin }}/api/webdav-v1/login/callback as one of your redirect URIs.
Set up OFBA configuration
Configure the ofba property in your chosen external IdP. For more information, see JWT parameters.
OFBA log in
Once configured, the login UI for OFBA should look like the following example image. In the example image, Keycloak is used as the external IdP.
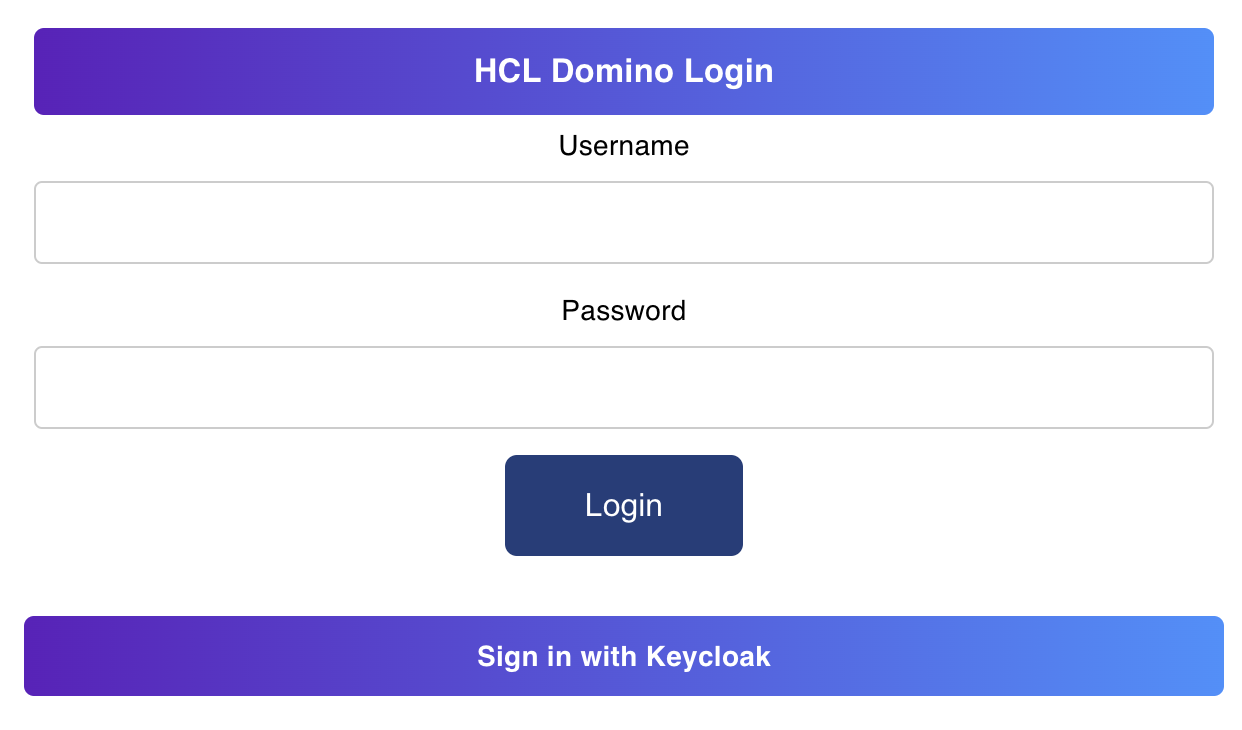
Clicking Sign in with {external_idp_name} commences the authorization code flow.
Note
Office Round Trip Experience external IdP login uses authorization code flow with PKCE.
Examples
Azure
The following is an example configuration for Azure IdP:
{
"jwt": {
"AzureIdP": {
"active": true,
"providerUrl": "https://login.microsoftonline.com/{tenant_id}/v2.0/.well-known/openid-configuration",
"aud": "{client_id}",
"iss": "https://login.microsoftonline.com/{tenant_id}/v2.0",
"algorithm": "RS256",
"ofba": {
"active": true,
"client_id": "{client_id}",
"application_id_uri": "api://dominorest/"
}
}
}
}
Keycloak
The following is an example configuration for Keycloak IdP:
{
"jwt": {
"KeycloakIdP": {
"active": true,
"providerUrl": "https://{keycloak_host}/realms/{realm_name}",
"ofba": {
"active": true,
"client_id": "{client_id}"
}
}
}
}