Configure Microsoft Entra ID as IdP
About this task
The procedures guide you on configuring Microsoft Entra ID, formerly Azure Active Directory, as an IdP. Microsoft Entra ID has its own ideas about JWT compatibility:
- The
audproperty is fixed to the ID of the application, not as commonly, the URL of the target system. - There is no
scopeproperty, but insteadscpto describe the requested scopes.
Client Ids
When configuring an external IdP using OIDC or OIDC-idpcat, you need to provide a clientId. It's recommended to use Domino, but the admins of your IdP might have other ideas. In any case, that's the clientId for the REST server. It's NOT the one for the Admin UI or the Office Forms Based Authentication (OFBA) for attachment editing. To be fully operational, you need to configure at least three clients on your IdP:
Dominofor the server (client secret might be handeled byidpcat.nsf).keepadminuifor the Domino REST API admin client. If you also want to use your IdP for Domino REST API Admin UI login.keepofbafor the Office document round trip experience. If you also want to use your IdP for Domino REST API OFBA round trip editing authentication.- One each for your custom client applications (with clientSecret for servers or PKCE for clients).
Use the internal IdP as learning resource
The application configuration provided by the internal IdP makes it easy to configure and retrieve client-specific JWT that have all the required fields. Test your application with that and use the defined properties, scopes foremost, to requests the external IdP client configurations.
Configuration in Azure
Register an application
-
Navigate to the Azure Portal to login, and then select App registrations.
-
Select New registration.
-
Enter a Name, select a supported account type (in most cases Single tenant will do), enter local redirect URL (so you can develop your app), and then click Register.
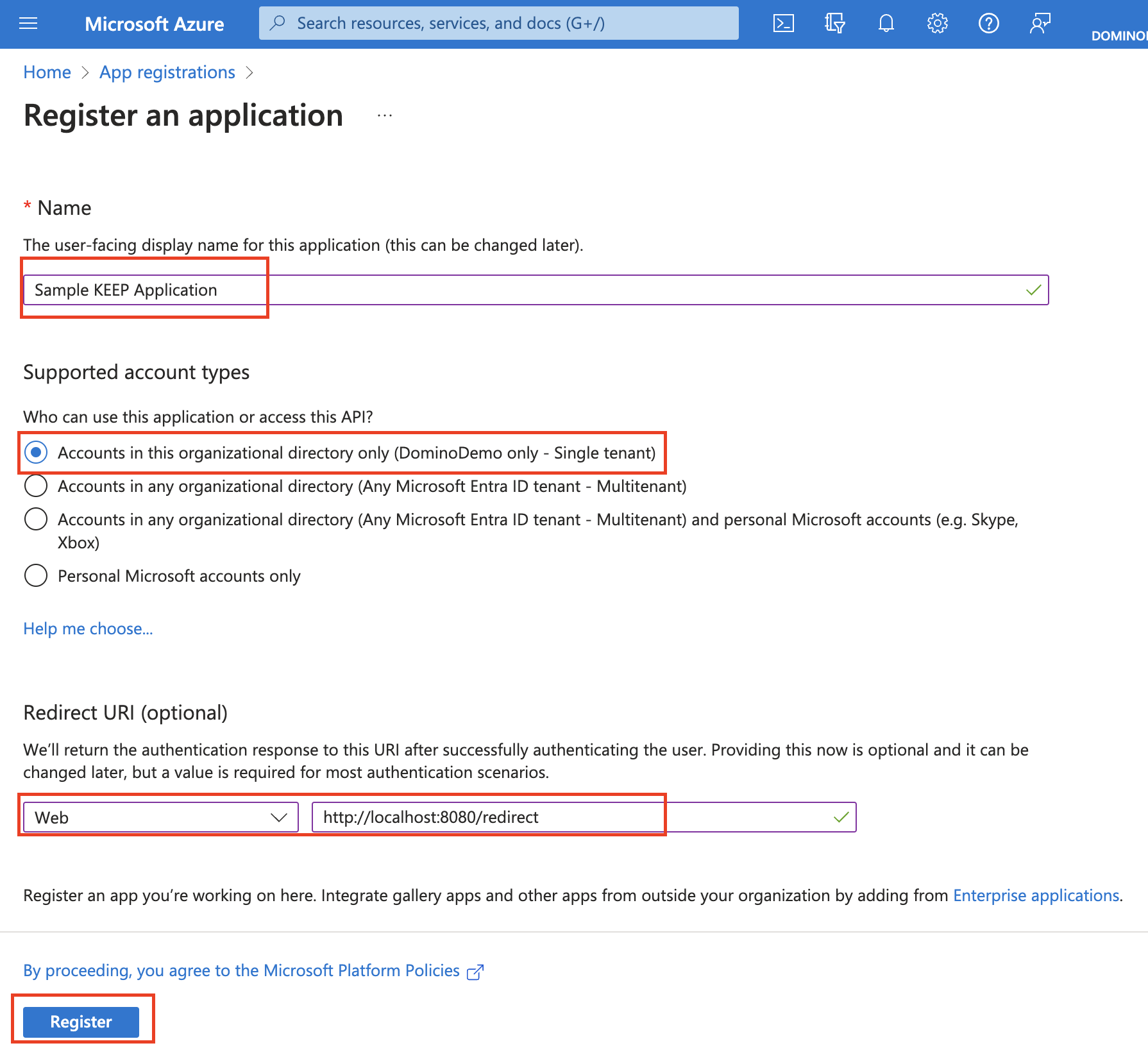
Tip
If you aren't sure about the redirect URL, use http://localhost:8080/redirect. You can change this later on in Authentication in the application page.
Add credentials
The next step is to add the client credentials. Your application will need the Application (client) ID and Client credentials.
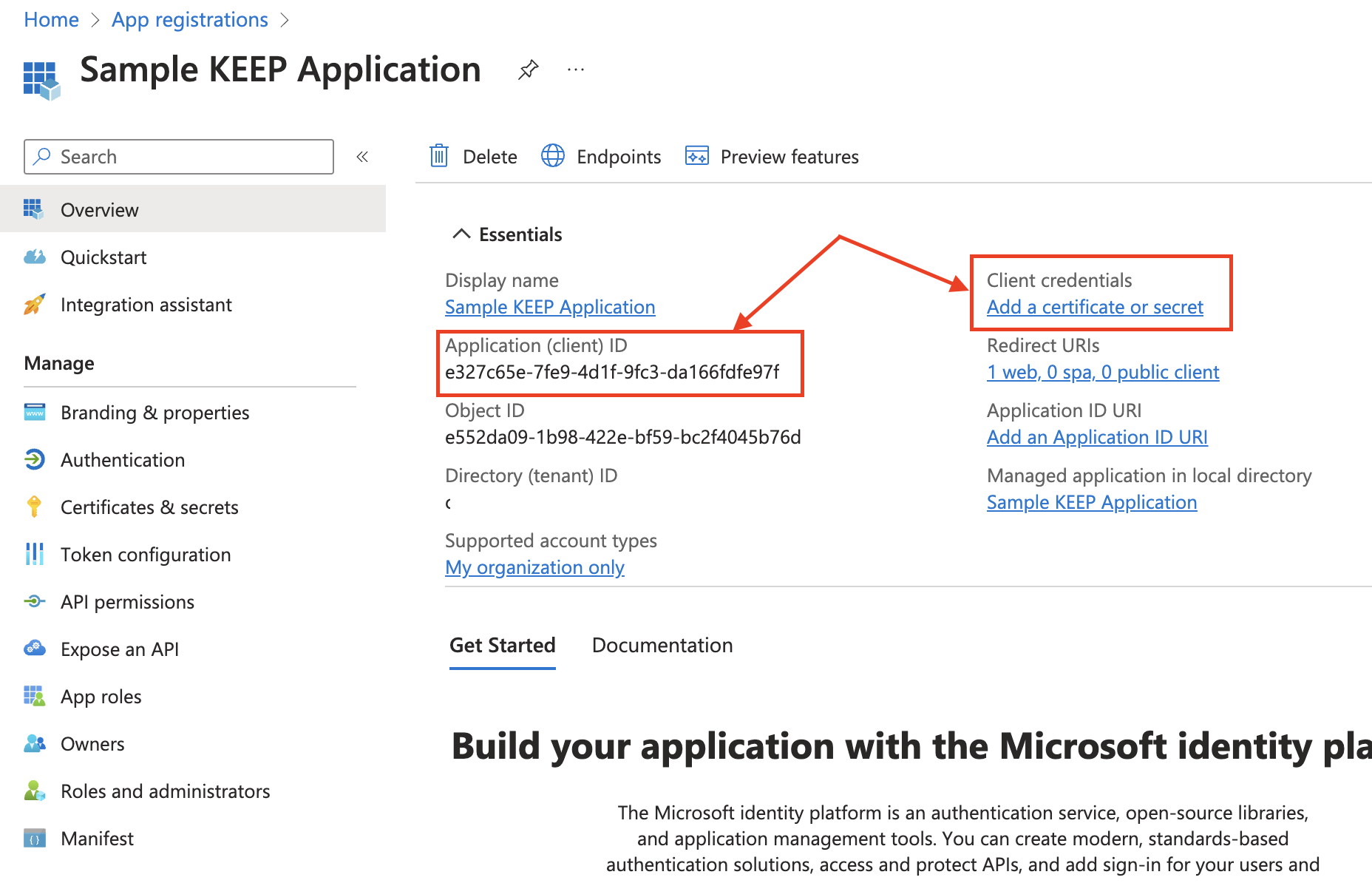
-
Select Certificates & secrets → Client secrets → New client secret.
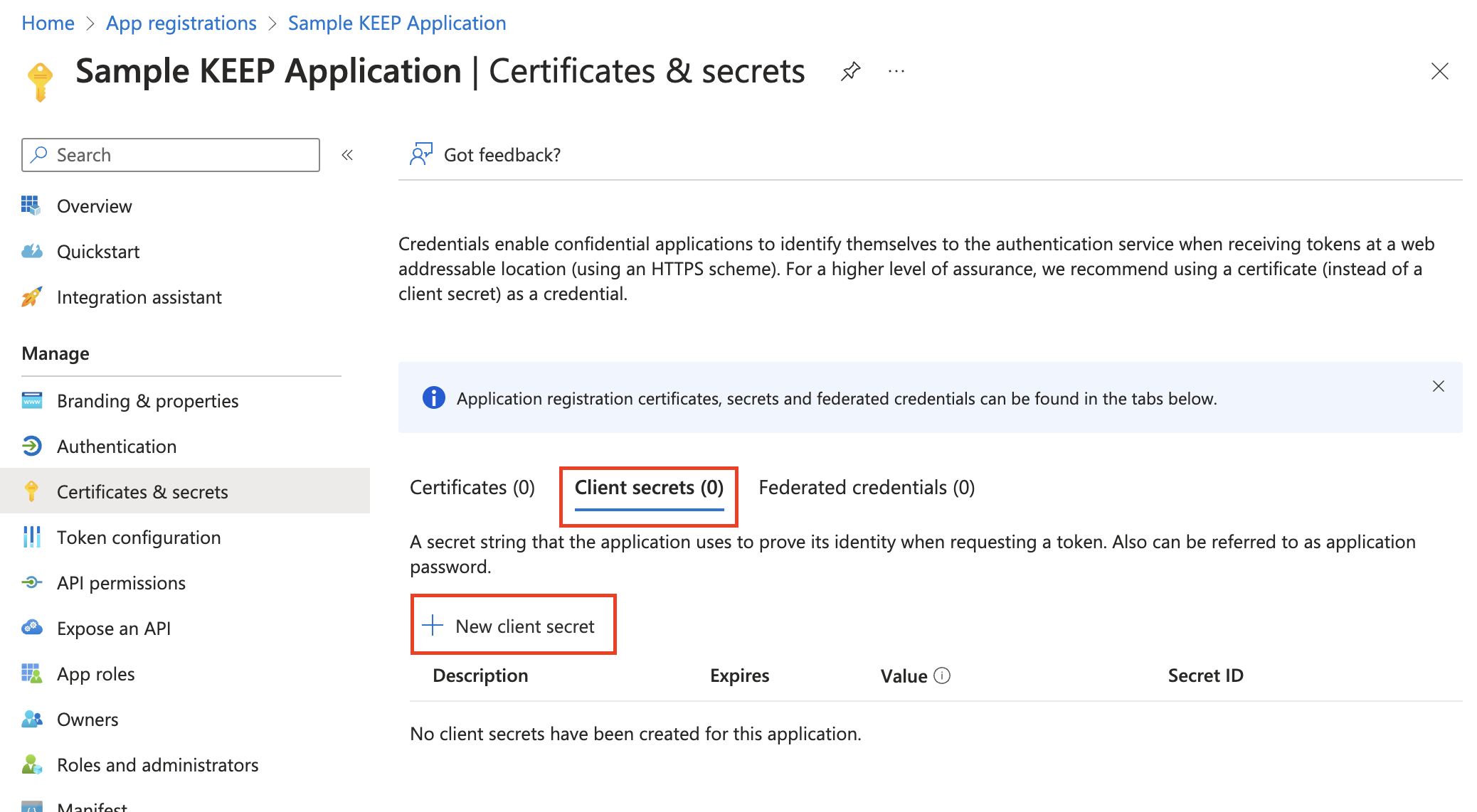
-
Add a description, select an expiration for your client secret, and then click Add.
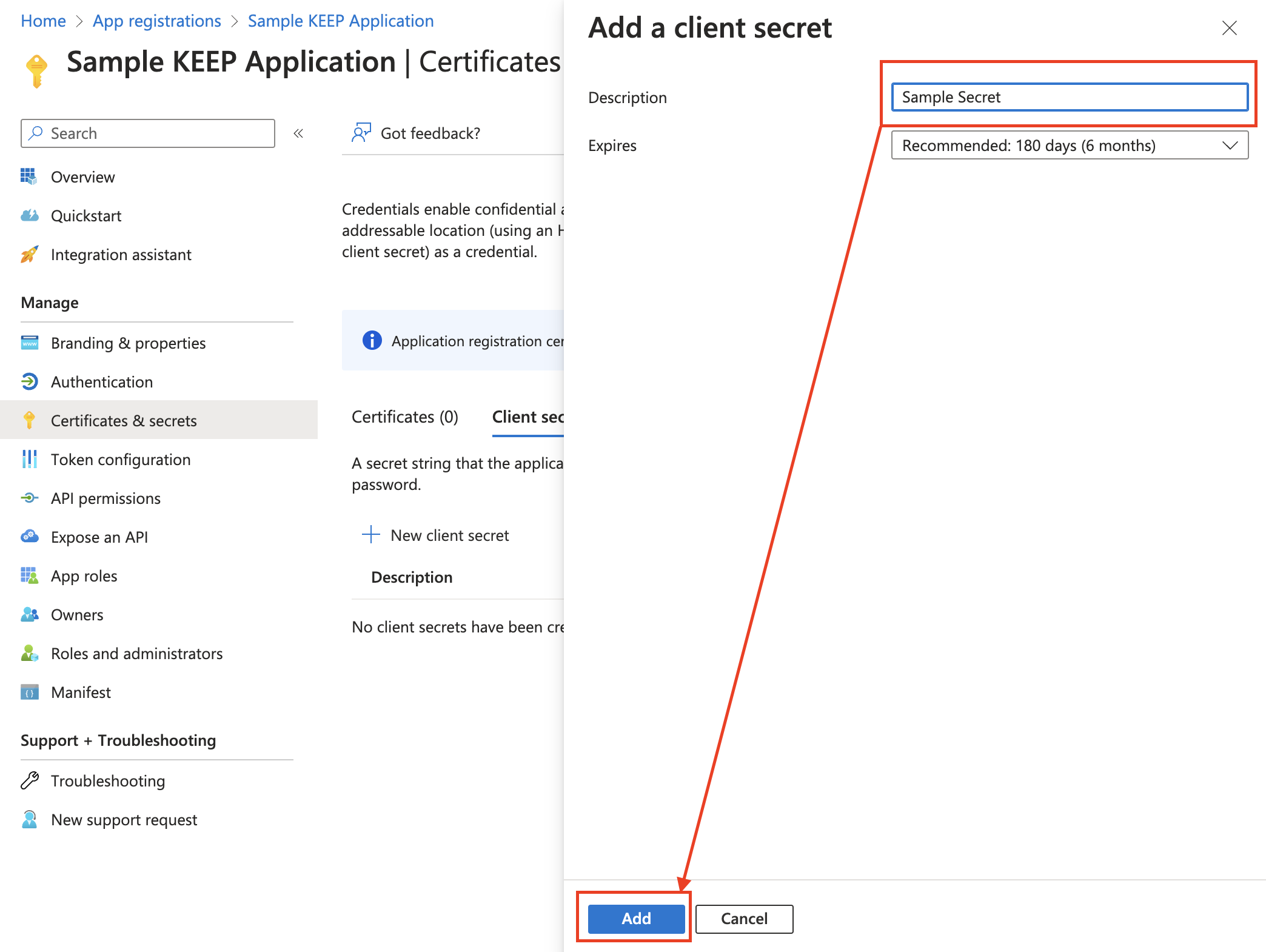
-
Copy the secret's value for use in your client application code.
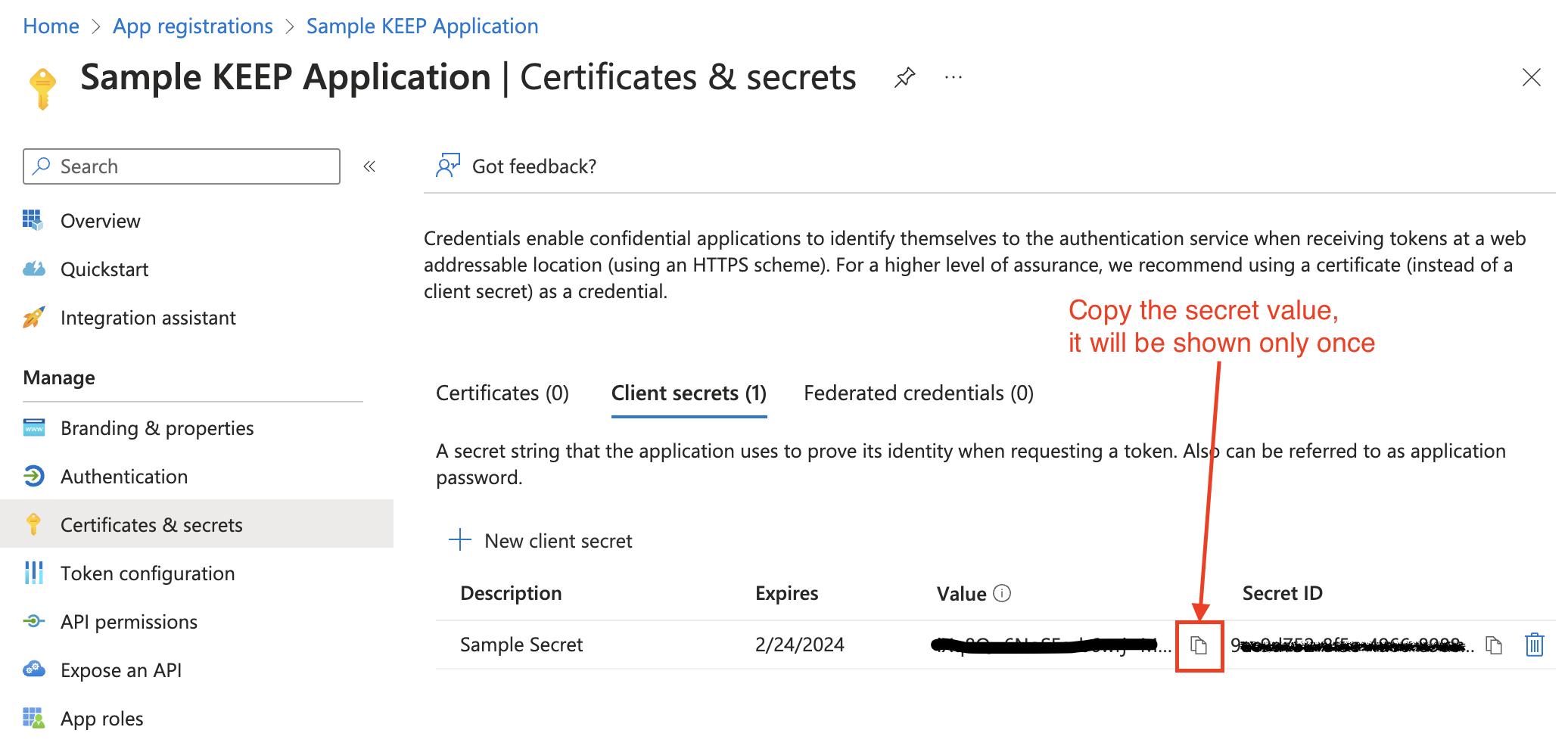
Note
The secret value is only shown once and never displayed again after you leave this page.
API definition
- Select Expose an API.
-
Select Add next to the Application ID URI. The URI must start with
api://. You can overwrite the UUID with some clear text name.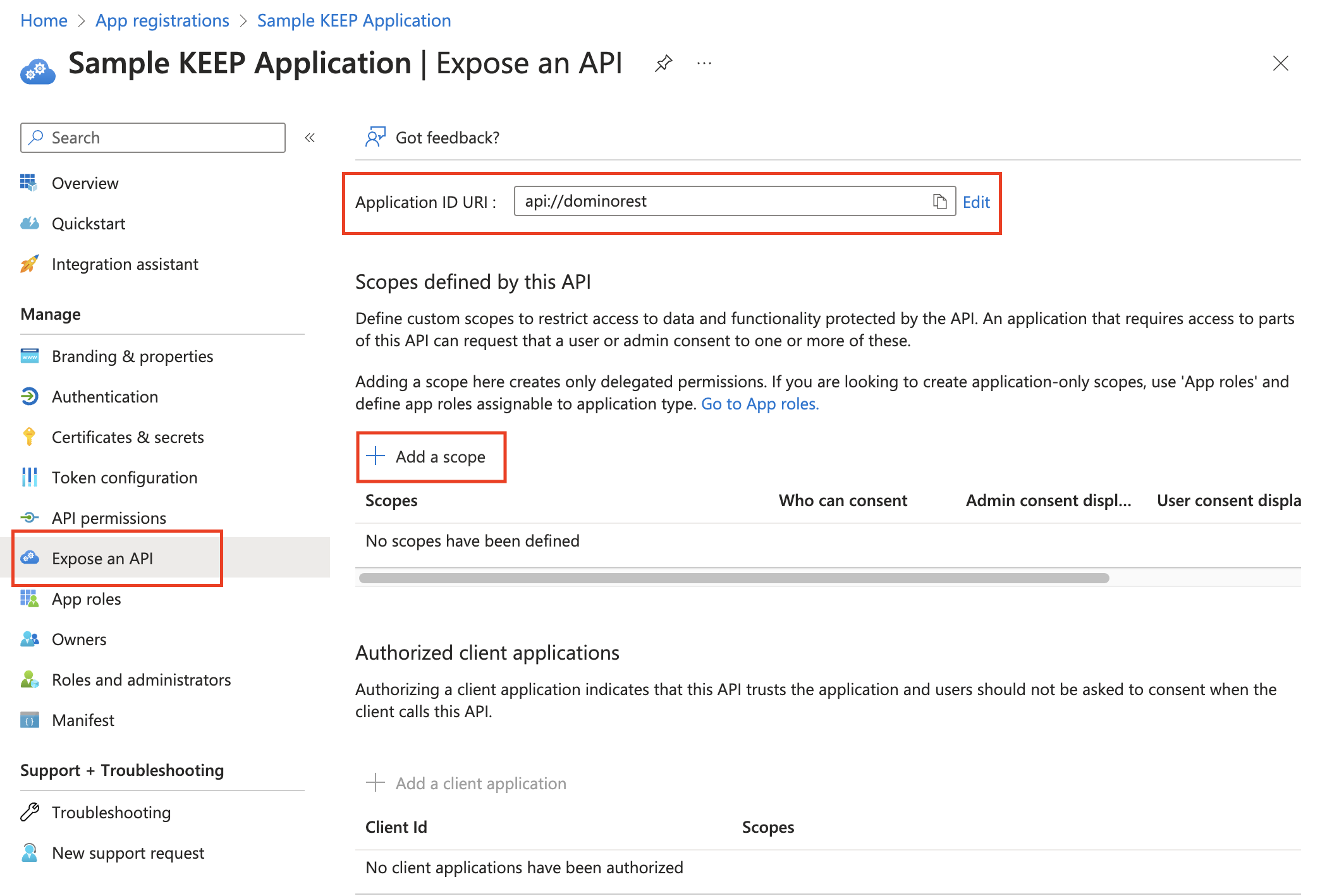
-
Select Add a scope.
-
Specify the scope's attributes in the Add a scope pane.
Ensure admins and users can consent and that the scope is set to Enabled. For more information about scopes in Domino REST API, see scopes reference and scope topic guide.
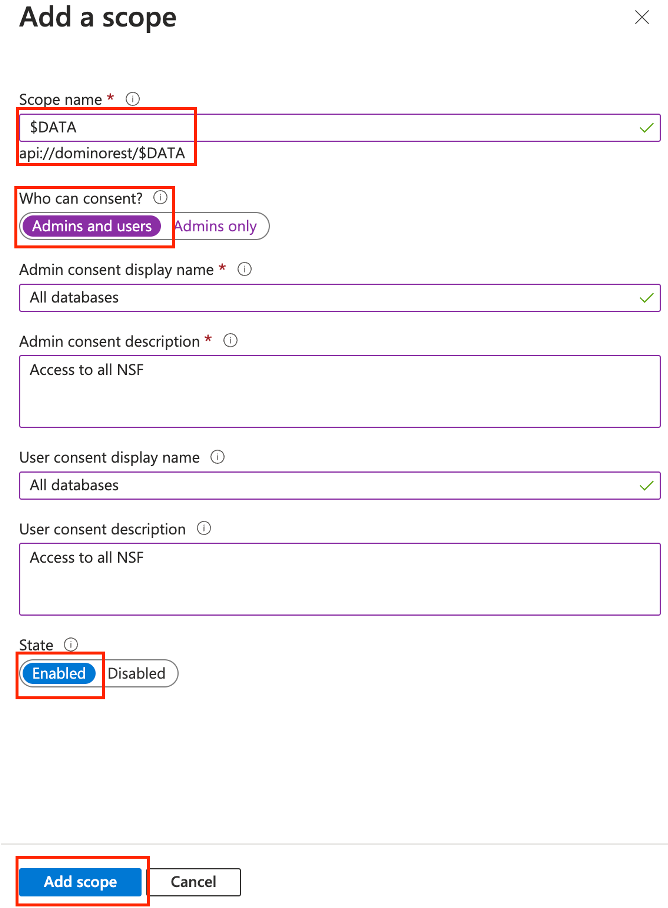
-
Click Add scope.
-
Repeat the steps for adding a scope for each scope that your need to add.
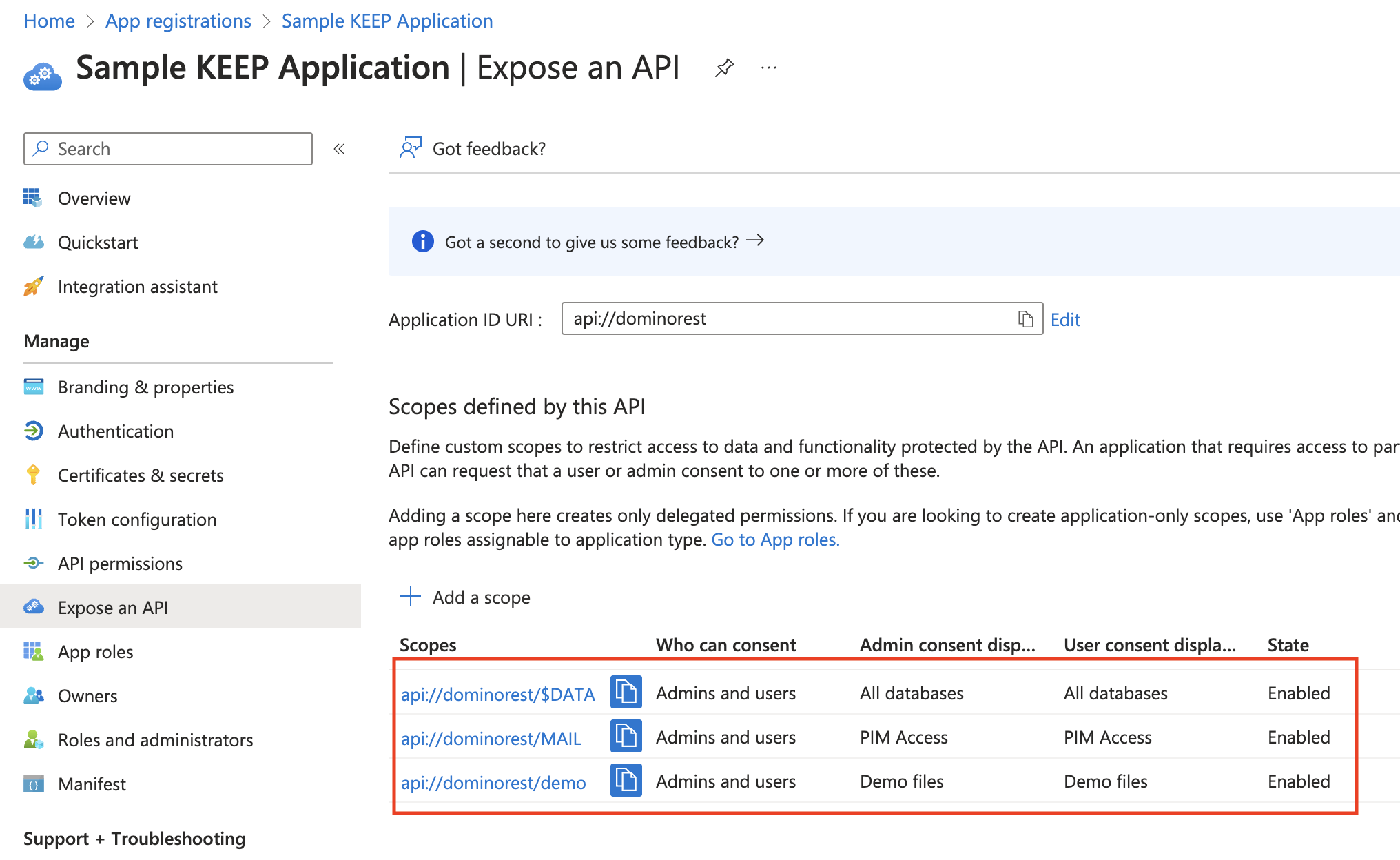
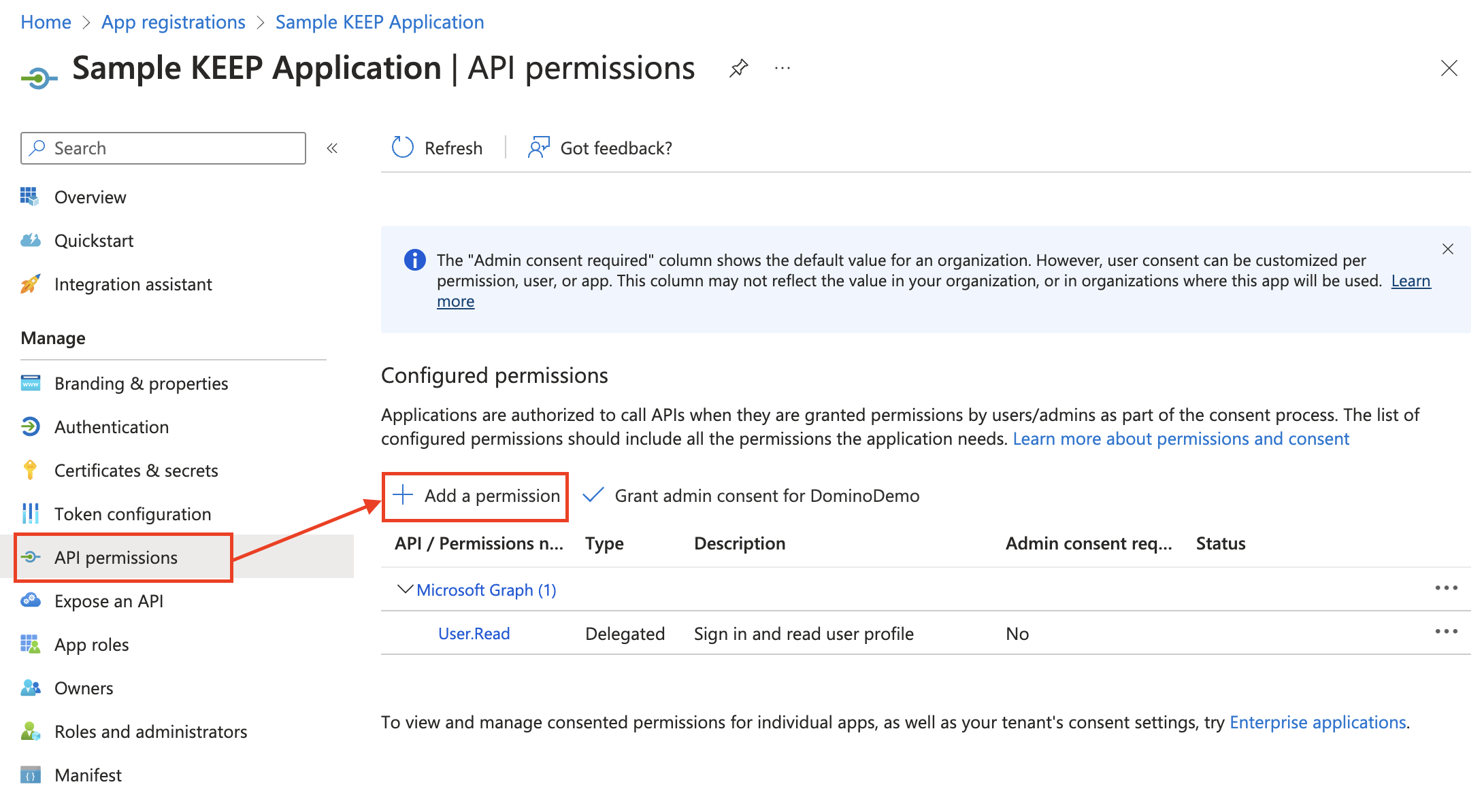
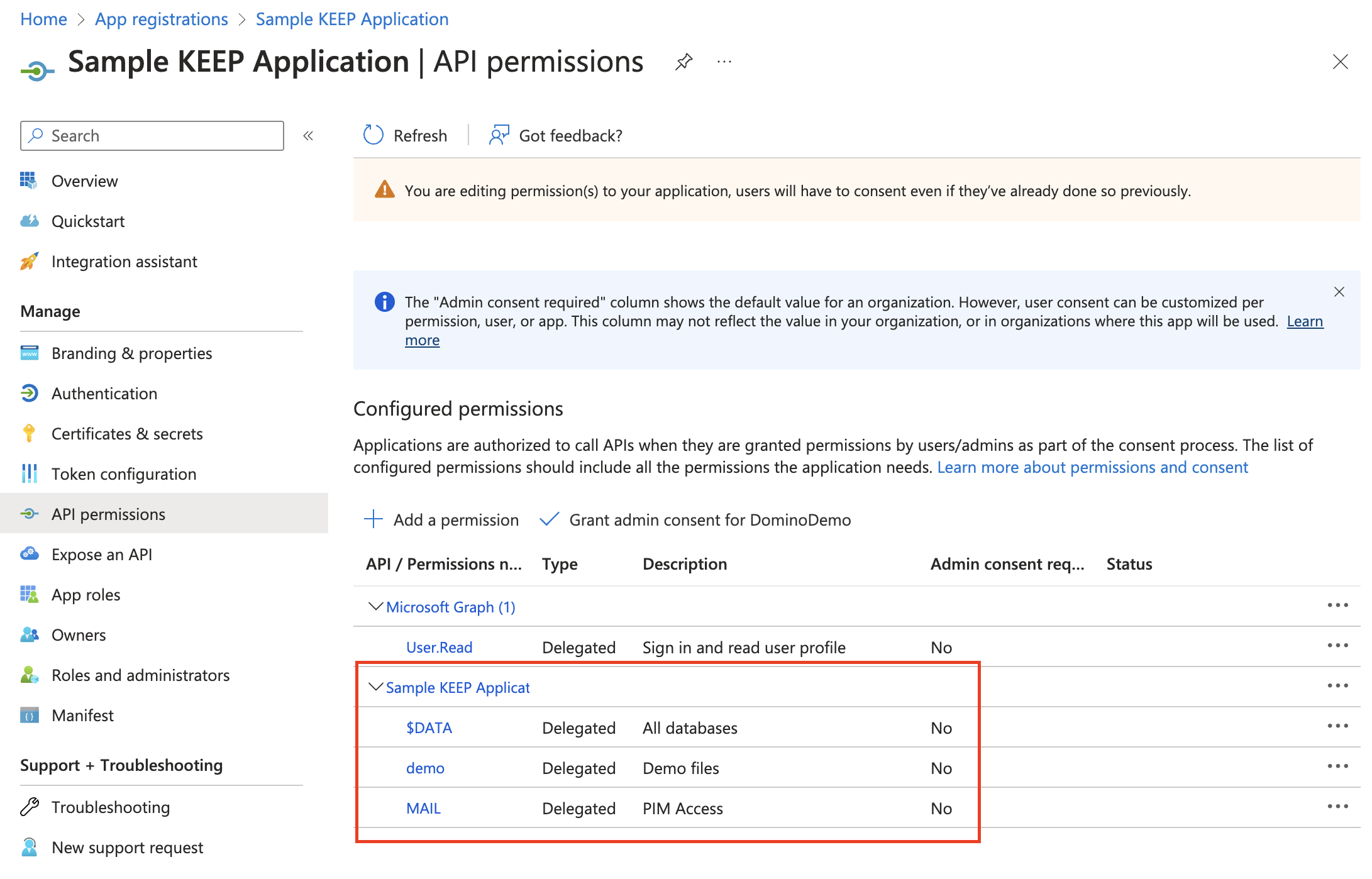
Configure API permissions
- Select API permissions. The API permissions screen, which has
User.Readpreconfigured, opens. -
Click Add a permission.
-
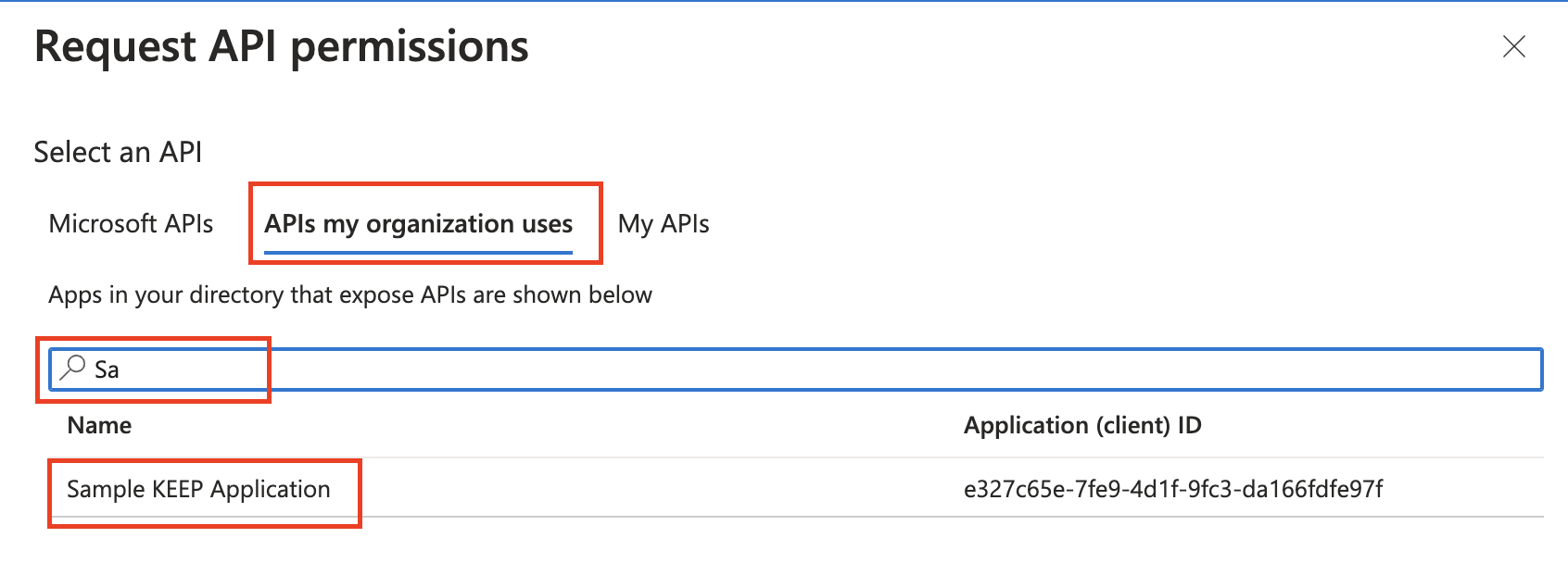
Select APIs my organization uses.
-
Start typing the name of your application, and then select it.
-
Under Select permissions, select the scopes you have created earlier and the click Add permissions.
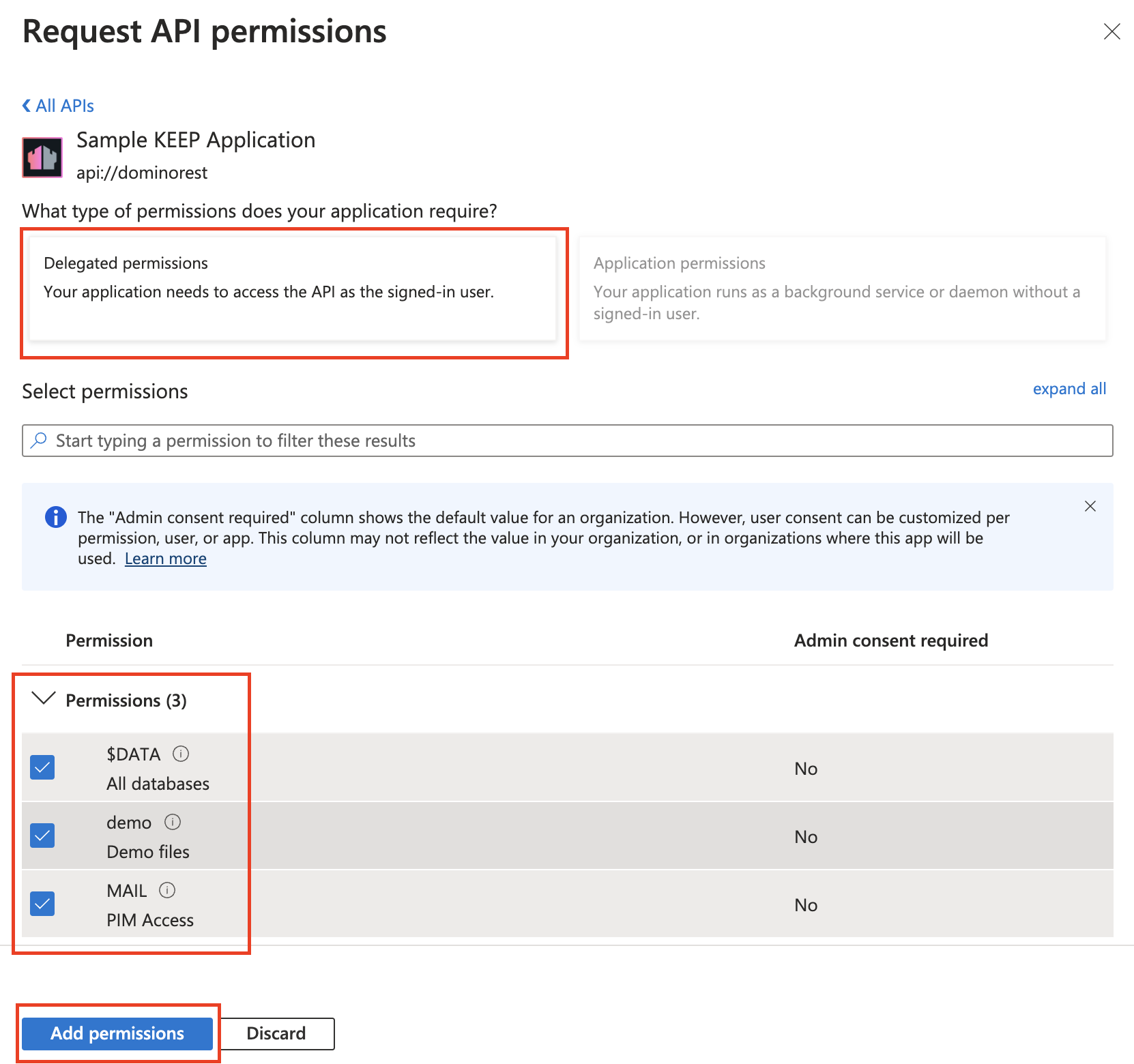
After adding permissions, you should see the selected permissions under Configured permissions.
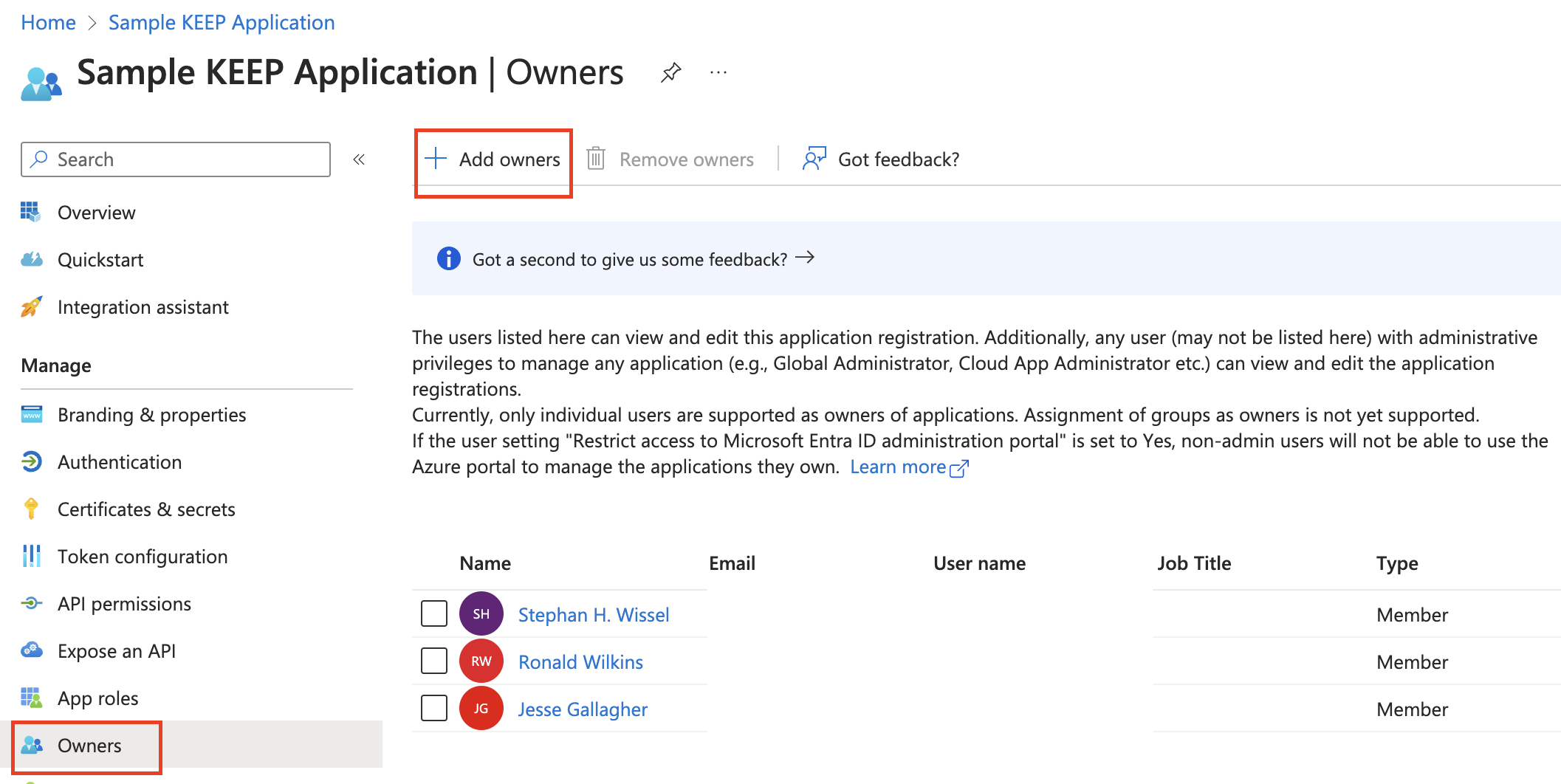
Update the application owners
-
Under Manage, select Owners and then select Add owners.
-
Search for and select the user account that you want to be an owner of the application, and then click Select.
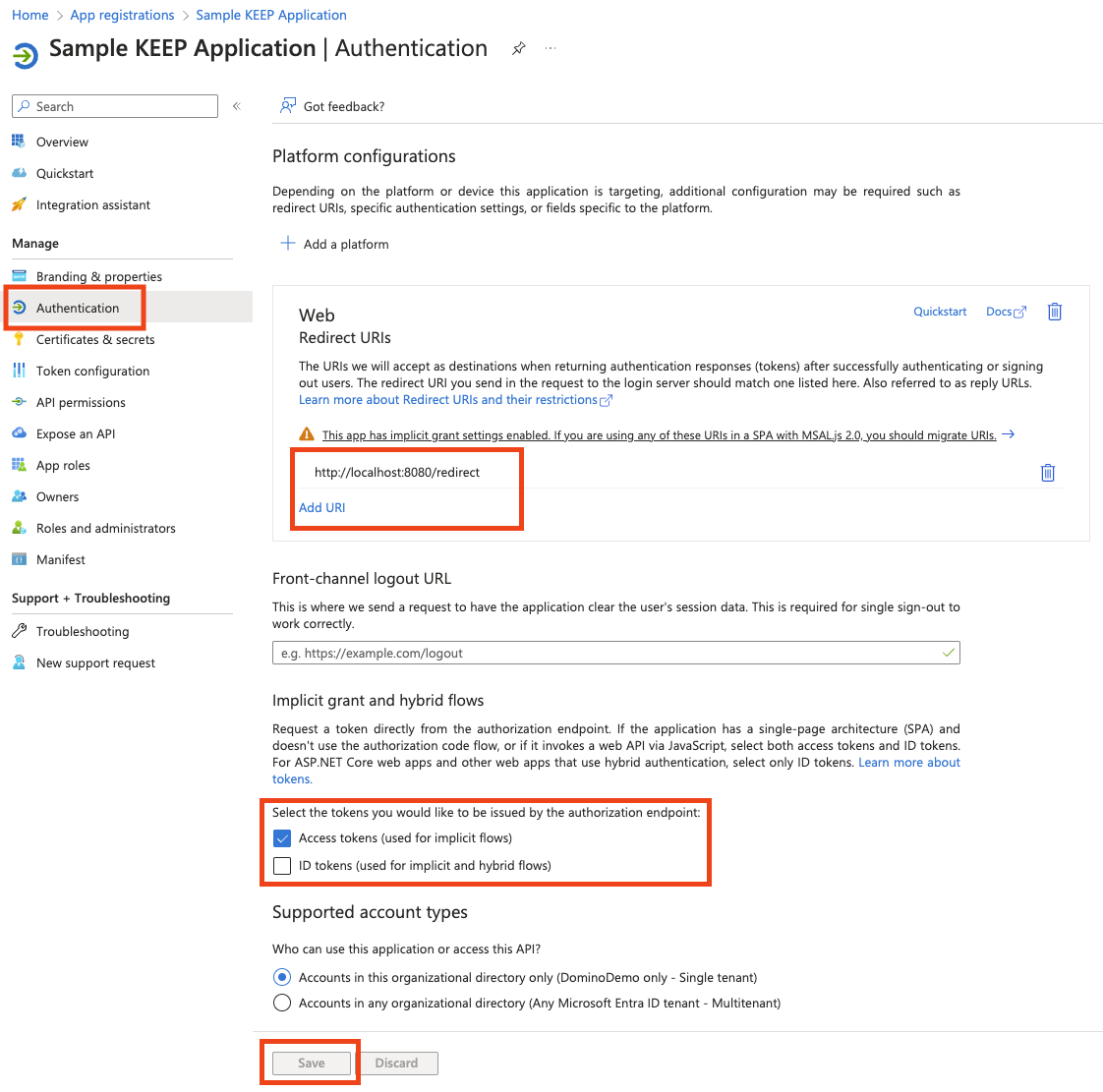
Adjust authentication
In Authentication, make sure you have localhost for local development and https-based URLs for your test, staging, and/or production systems specified. Select only Access token and make sure redirect ends with /.
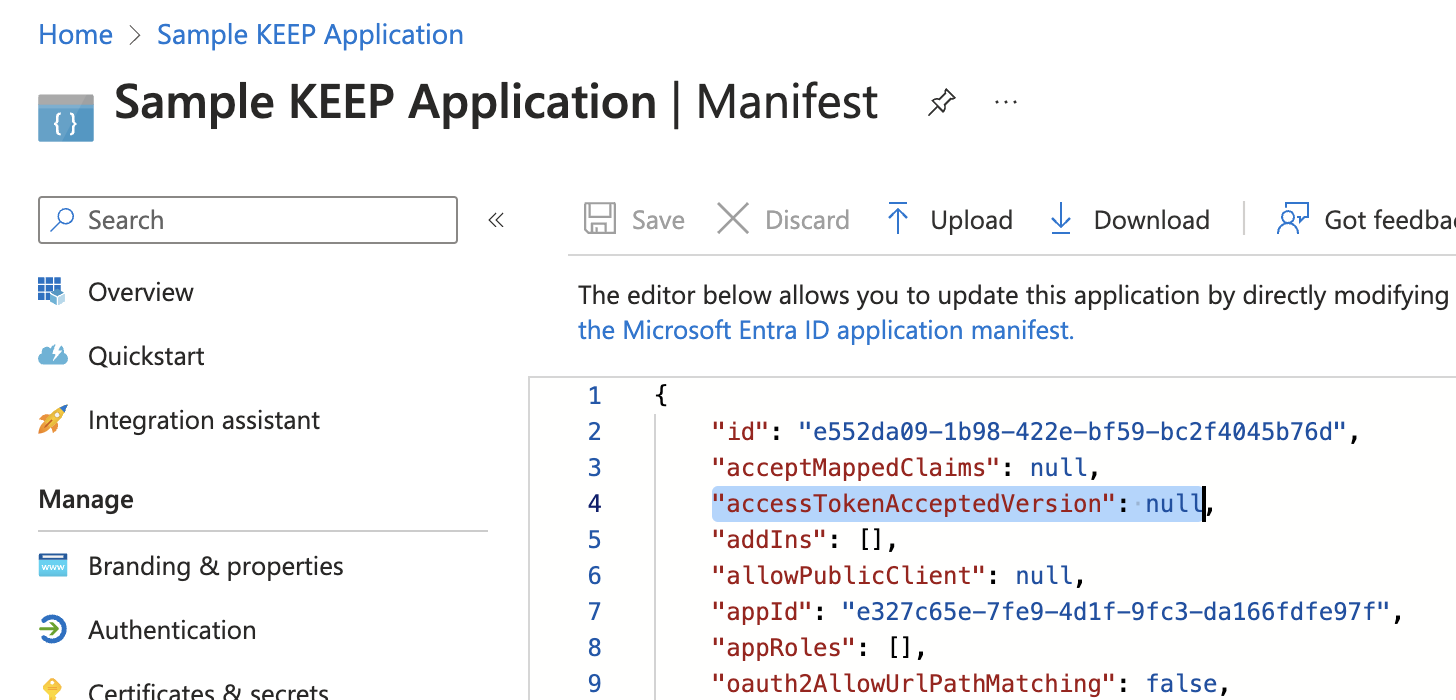
Adjust app manifest
- Under Manage page, select Manifest. A web-based manifest editor opens, allowing you to edit the manifest within the portal.
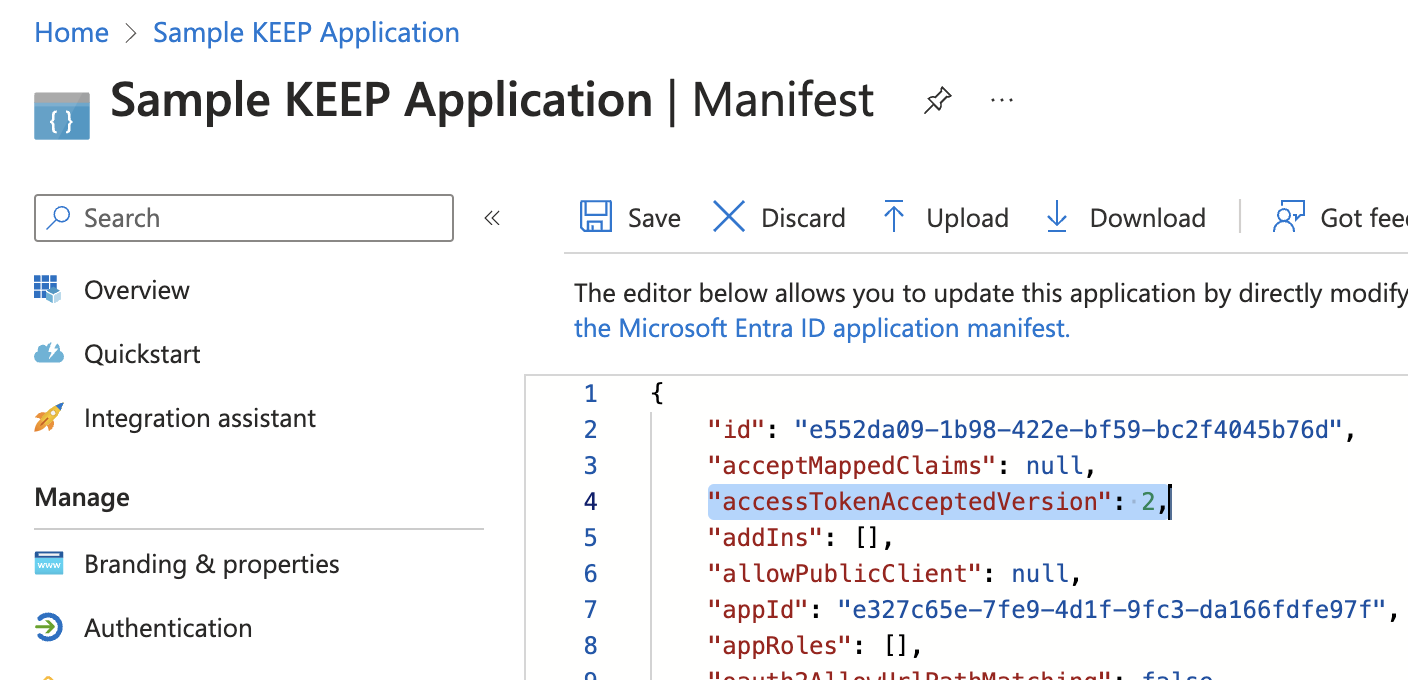
- Change the value of
accessTokenAcceptedVersionfromnullto2.
Before change:
After change:
URLs to note
-
From the app's Overview page, select Endpoints.
-
Take note of the following URLs.
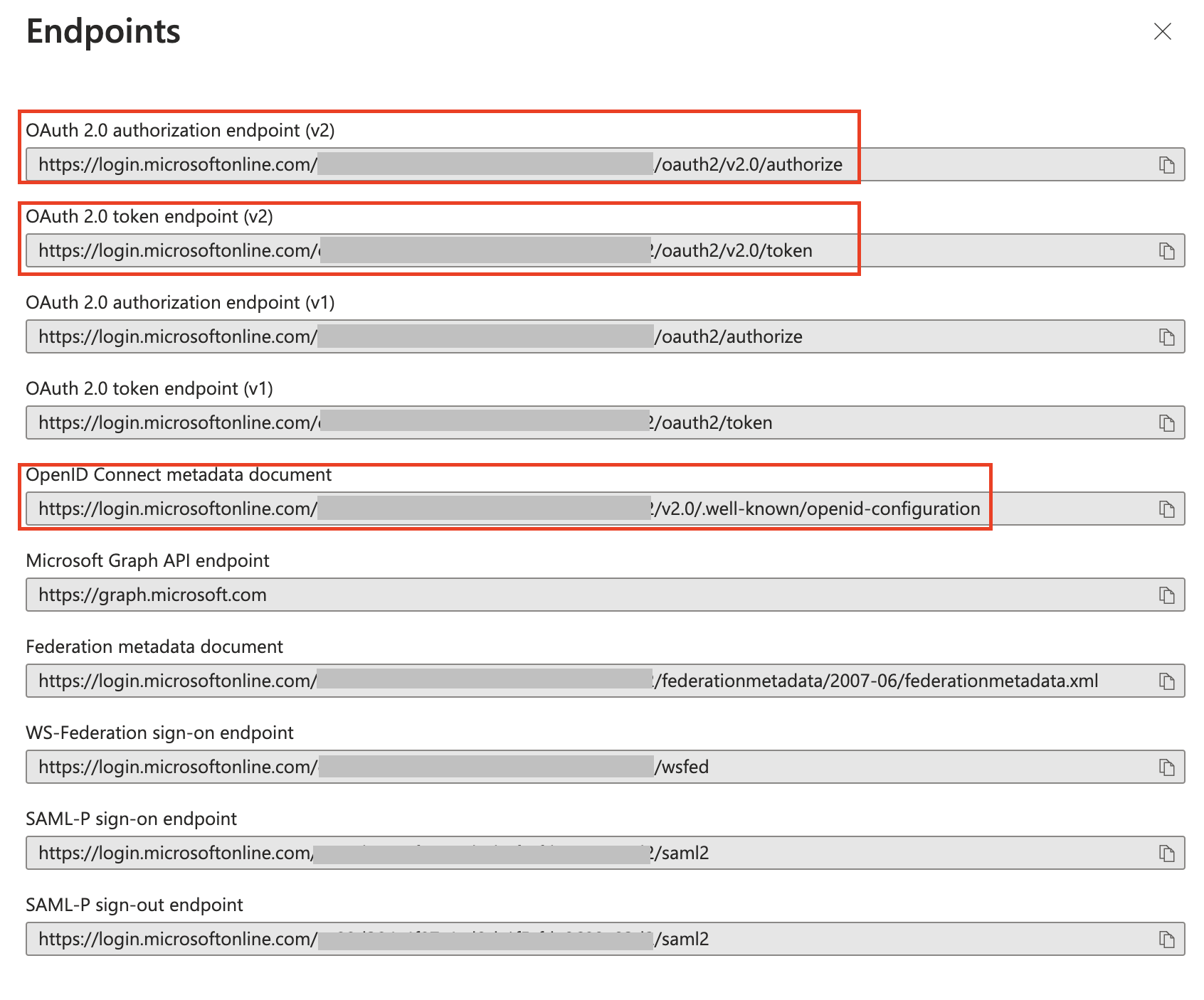
All URLs are retrievable by accessing the OpenID Connect metadata document, colloquially referred to as .well-known. These are the ones involved:
- OpenID Connect metadata document
- OAuth 2.0 authorization endpoint (v2)
- OAuth 2.0 token endpoint (v2)
Configuration in Domino REST API
-
Create a json file in the directory
[notesdata]/keepconfig.d.You can choose the filename as long as you limit yourself to numbers and ASCII letters (
[0-9a-zA-Z]+). We suggestAzureAD01.json, the same value you use in the json data below. -
Add the following content to the json file.
{ "jwt": { "AzureIdP": { "active": true, "providerUrl": "https://login.microsoftonline.com/[your-tennantid-here]/v2.0/.well-known/openid-configuration", "aud": "[your-client-id-here]", "iss": "https://sts.windows.net/[your-tennantid-here]/", "algorithm": "RS256" } } }Remarks:
- The
AzureAD01isn't a fixed value. Pick anything that makes it clear for you. Use the value as the filename too. - The
audparameter is the Application ID in Add credentials. - The
issparameter might be different from what theopenid-configurationreports. Compare the values. It has been noticed that the URL changed fromhttps://login.microsoftonline.com/[your-tennantid-here]/v2.0tohttps://sts.windows.net/[your-tennantid-here]/, if that's so you need to specify it here. - Currently, Azure AD doesn't return the
algclaim in thejwks_uri. You have to specify it here.
- The
-
Restart Domino REST API.
Azure AD / Entra ID is a moving target
Depending on your configuration, you will need to adjust the aud and iss values in the configuration file. To determine the correct values, use the test application below to inspect what values are actually sent with the Azure access token. For aud, you might get the application ID and something different for iss. Also, the algorithm might be included somewhere. Use the test application below!
Test the application
-
Go to Downloads, and then download the
AzureTester.zipfile.The file contains an expressJS application and related static files (HTML/CSS/JS).
-
Extract the zip file.
-
Navigate to the directory and run the web server using the following command:
NodeJS required
You need a current NodeJS version installed.
npm install node server.jsNo production use of the code
Do NOT use this code in production.
-
Open the URL http://localhost:8080/ and fill in the form details. You will find most of the values in the overview page of the Azure application registration. You should see a page like this:
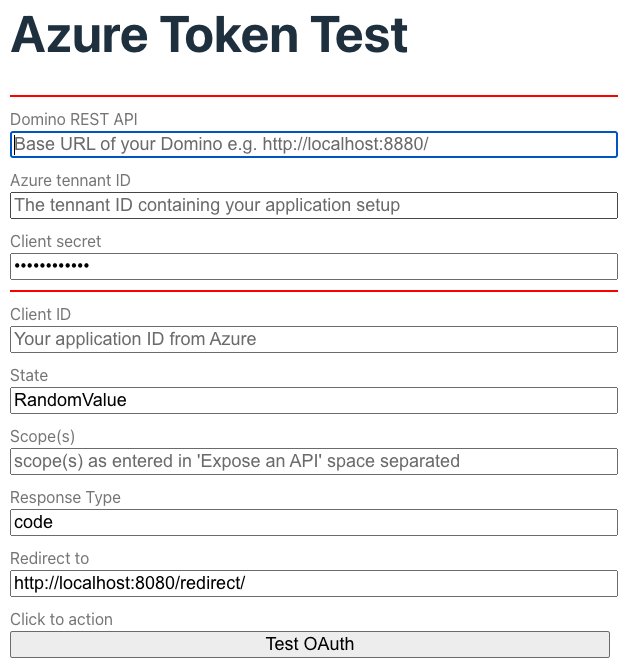
Include the Application ID URI
When you specify the scopes, you need to include the "Include the Application ID URI" in the test form. The URI will be stripped from the resulting JWT token.
So to get scp : "$DATA MAIL demo" in the JWT, you must specify api://dominorest/$DATA api://dominorest/MAIL api://dominorest/demo where api://dominorest is whatever you specified as Application ID URI.
Azure redirects you to the /redirect URL. Typically, this page would auto process, but you want to marvel at the authorization code. When you click Exchange token, the ExpressJS server exchanges the code for a JWT and returns the list of configured endpoints as example. You can't do this with the browser alone, CORS prevents it.
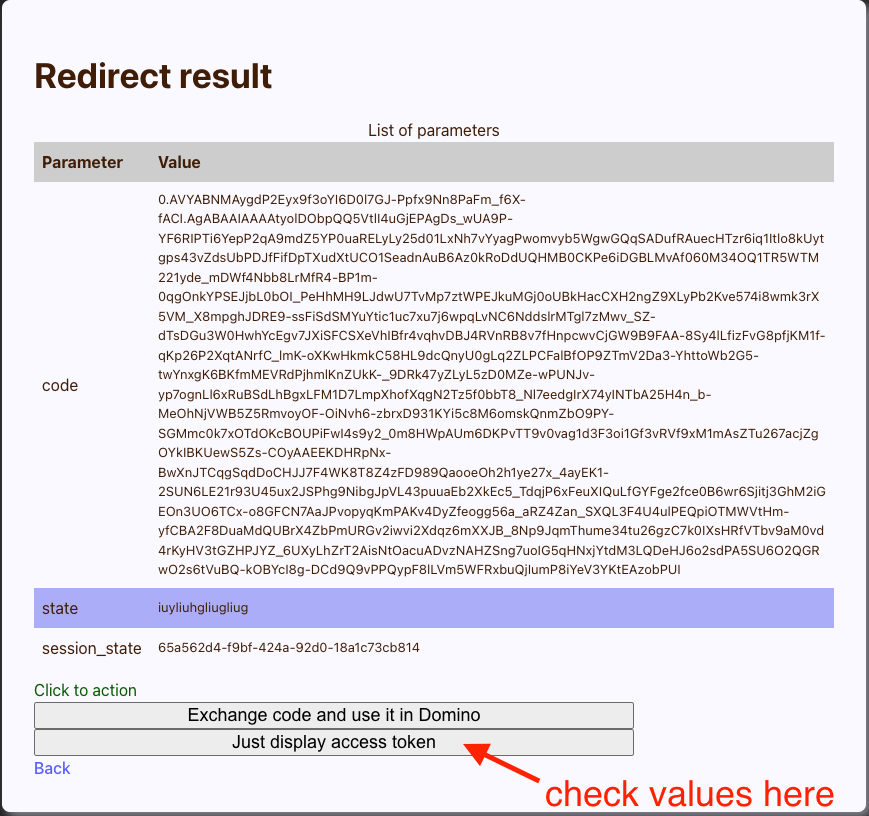
Check the results:
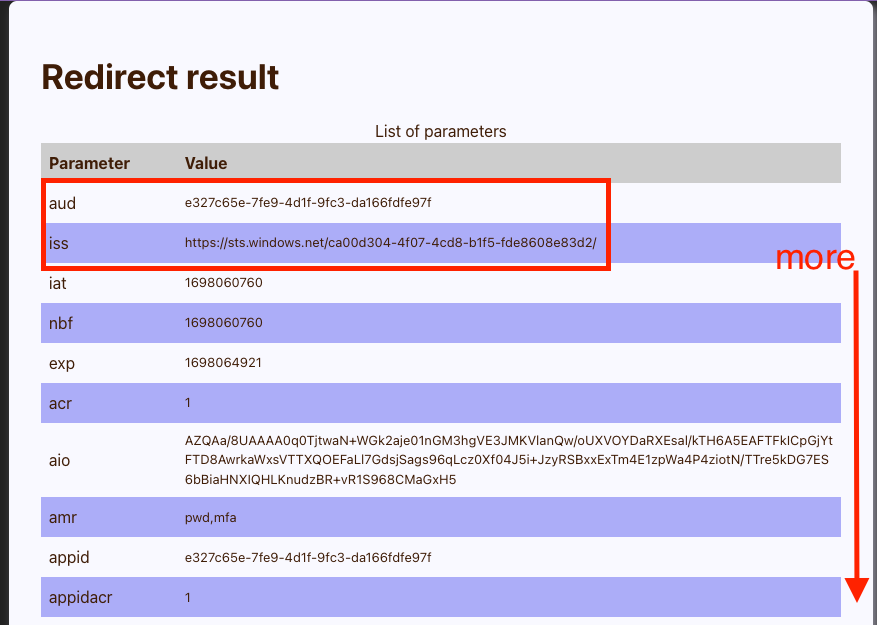
Troubleshooting
A few tips to troubleshoot the setup when the goalpost has been moved:
-
Grab the JWT token and paste it at the JWT.io website to decode the JSON payload.
-
If your corporate policy prohibits that, then extract the string between the two
.from your JWT token and send it through a Base64 decoder:echo [the string] | base64 --decode | jq. Kindly note that| jqis optional. - Compare the
issvalue from the JWT token with theissuervalue from theopenid-configurationendpoint. If they don't match, you need to add theissto the JSON configuration file you created or edited inkeepconfig.d. - Compare the
audvalue from the JWT token with theaudvalue of the configuration file. Adjust the configuration file if different. - Check the
scp, which is Microsoft's "alternative" toscope, and make sure it has the expected values matching the settings in the application configuration in the Admin UI. Adjust the scope in the DRAPI application (Admin UI) or your AzureAD IdP settings.