Setup external IdP for Office Round Trip Experience
Aside from the default Domino REST API login page, you can also use your configured external IdP for Office Round Trip Experience log in.
Configuration
Set up external IdP
Configure your external IdP in the configuration file. For more information, see configuring external IdP for configuring an external IdP of your choice.
Note
When configuring your external IdP, make sure to set {{ origin }}/api/webdav-v1/login/callback as one of your redirect URIs.
Set up OFBA configuration
Configure the ofba property in your chosen external IdP. For more information, see JWT parameters.
OFBA log in
Once configured, the login UI for OFBA should look like the following example image. In the example image, Keycloak is used as the external IdP.
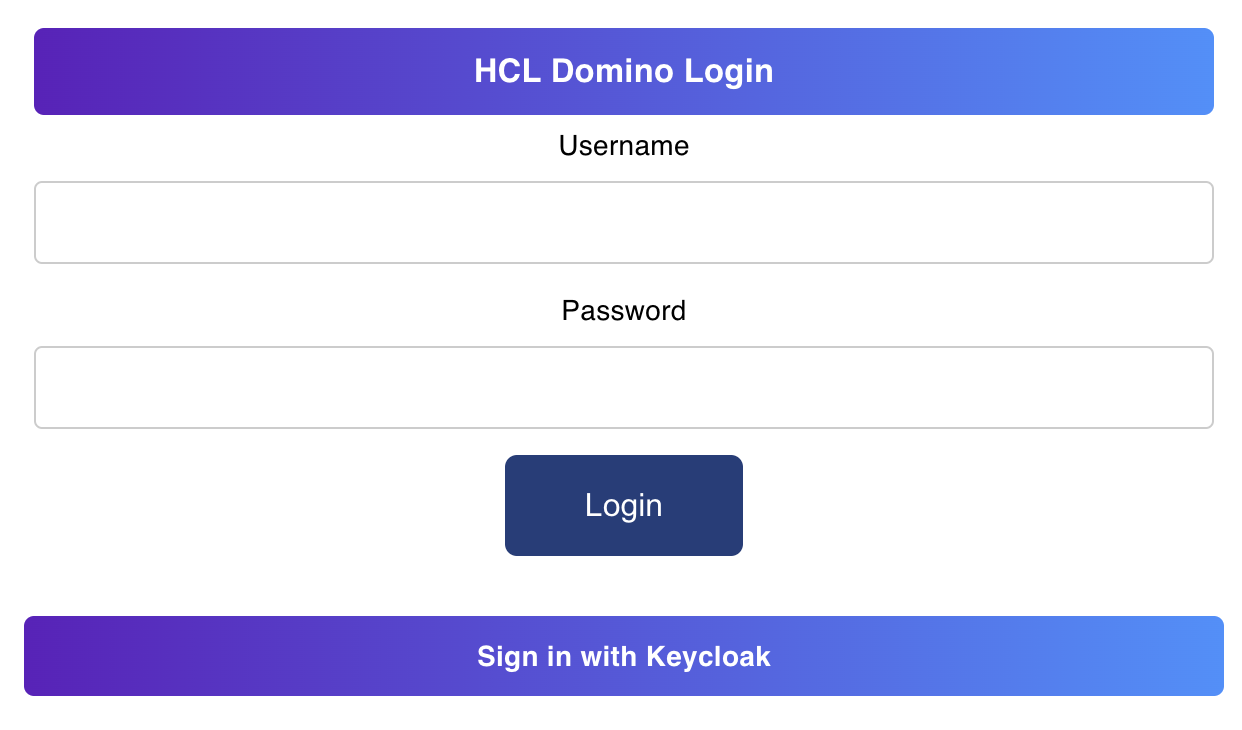
Clicking Sign in with {external_idp_name} commences the authorization code flow.
Note
Office Round Trip Experience external IdP login uses authorization code flow with PKCE.
Examples
Azure
The following is an example configuration for Azure IdP:
{
"jwt": {
"AzureIdP": {
"active": true,
"providerUrl": "https://login.microsoftonline.com/{tenant_id}/v2.0/.well-known/openid-configuration",
"aud": "{client_id}",
"iss": "https://login.microsoftonline.com/{tenant_id}/v2.0",
"algorithm": "RS256",
"ofba": {
"active": true,
"client_id": "{client_id}",
"application_id_uri": "api://dominorest/",
"scope": ["$DATA"]
}
}
}
}
Keycloak
The following is an example configuration for Keycloak IdP:
{
"jwt": {
"KeycloakIdP": {
"active": true,
"providerUrl": "https://{keycloak_host}/realms/{realm_name}",
"ofba": {
"active": true,
"client_id": "{client_id}",
"scope": ["$DATA"]
}
}
}
}